Assuming we have two Virtual Private Clouds (VPCs) designated as follows:
Green VPC – greenvpc01
Red VPC – redvpc01
We will now provide the IP CIDR allocations for the aforementioned VPCs.
VPC Name | IPv4 CIDR | Subnet Name | Subnet CIDR | Routes Name | Internet Gateway | Peering |
redvpc01 | 192.168.0.0/24 | redvpc-subnet01 | 192.168.1.0/24 | redvpc-route01 | redvpc-igw01 |
|
greenvpc01 | 10.5.0.0/16 | greenvpc-subnet01 | 10.5.1.0/16 | greenvpc-route01 | greenvpc-igw01 |
|
VPC Create:
Go to VPC and click on Create VPC, you see the similiar kind of page below
Provide the VPC name, IPV4 CIDR and click on create.
Amazon Web Services (AWS) offers a Virtual Private Cloud (VPC) that allows users to create a logically isolated network environment. This service enables the configuration of various network settings, such as IP address ranges, subnets, route tables, and network gateways, providing users with complete control over their virtual networking resources.
With AWS VPC, you can securely launch AWS resources, such as Amazon EC2 instances, within a defined virtual network. Additionally, VPC supports features like security groups and network access control lists (ACLs) to enhance security and manage traffic flow. By utilizing VPC, organizations can tailor their cloud infrastructure to meet specific requirements while maintaining a high level of security and compliance.

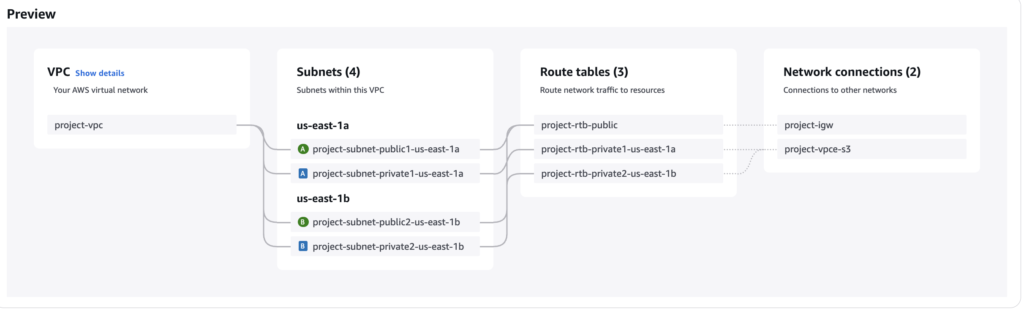
Note: If you select option VPC or more then it will automatically create required subnets, route tables and network connections such as internet gateway as like below. We are going manual option here.
To create a subnet, follow these steps:
Navigate to the subnets section.
Click on “Create Subnet.”
Fill in the required details as outlined in the table.
Note: You have the option to create multiple subnets based on your specific requirements.

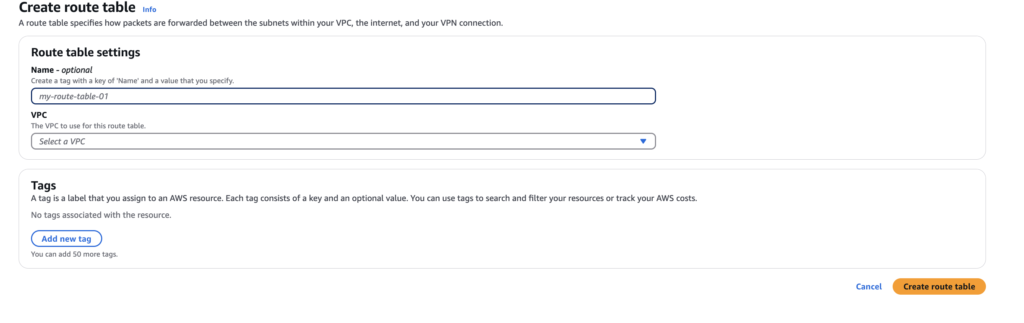
Now go to Route tables and create route ,selecting vpc in route
Route tables in AWS: An Overview
In Amazon Web Services (AWS), route tables are essential components of the networking infrastructure. They play a crucial role in determining how traffic is directed within your Virtual Private Cloud (VPC). Each route table contains a set of rules, known as routes, which dictate the destination of network traffic based on its IP address.
When you create a VPC, AWS automatically generates a main route table for you. You can also create additional route tables to suit specific networking needs. Each subnet in your VPC must be associated with a route table, which defines how traffic is routed to and from the subnet.
Understanding the configuration of route tables is vital for optimizing network performance and ensuring secure communication between resources. By effectively managing your route tables, you can control the flow of data, implement security measures, and enhance the overall functionality of your AWS environment.
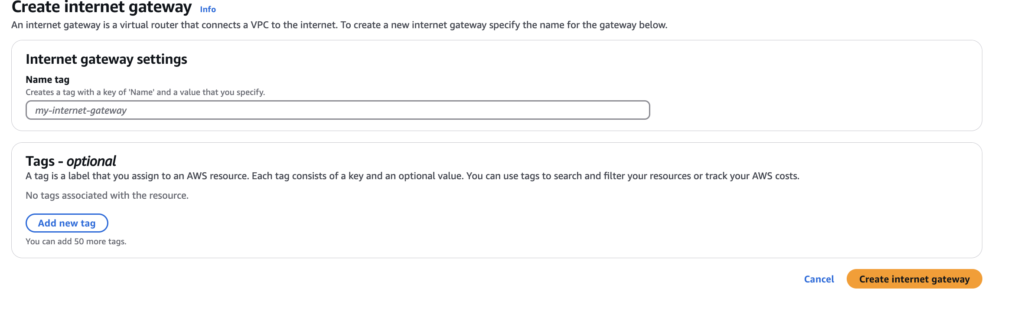
Goto Internet Gateway and create internet gateway
The Internet Gateway in Amazon Web Services (AWS) is a vital component that enables communication between instances in a Virtual Private Cloud (VPC) and the internet. It serves as a bridge, allowing outbound traffic from the VPC to the internet and facilitating inbound traffic from the internet to instances within the VPC.
By attaching an Internet Gateway to your VPC, you can assign public IP addresses to your instances, ensuring they are accessible from the internet. This setup is essential for applications that require direct internet access, such as web servers or public-facing applications.
Furthermore, the Internet Gateway supports both IPv4 and IPv6 traffic, providing flexibility for modern applications. Properly configuring route tables and security groups is crucial to ensure secure and efficient communication through the Internet Gateway.
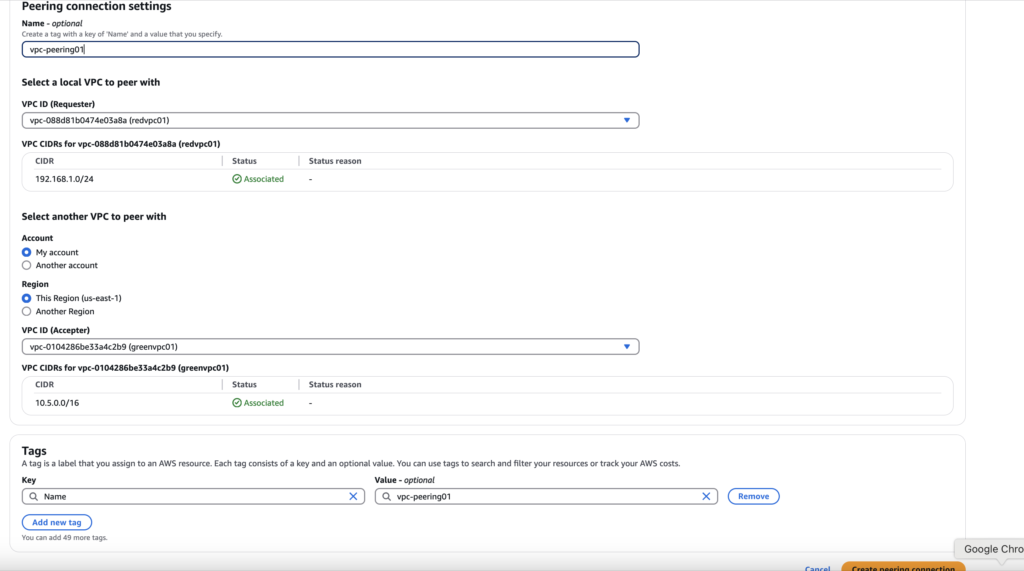
After creating both VPCs, navigate to the Peering section to establish communication through Peering. Here, create a peering connection and select the Accepter and Receiver VPCs.
Once the peering connection is established, accept it by going to the Actions menu and selecting “Accept.”
Peering in AWS (Amazon Web Services) refers to the process of connecting two Virtual Private Clouds (VPCs) to enable them to communicate with each other as if they were part of the same network. This setup allows for seamless data transfer and resource sharing between VPCs, enhancing the overall efficiency and flexibility of cloud architecture.
AWS offers two types of peering: VPC Peering and AWS Transit Gateway. VPC Peering allows direct connections between VPCs, while AWS Transit Gateway simplifies the management of multiple VPC connections by acting as a central hub.
Establishing a peering connection involves several steps, including configuring route tables and ensuring that security groups and network access control lists (ACLs) permit the desired traffic. It is essential to note that VPC peering is a one-to-one relationship, meaning each VPC can only be directly connected to one other VPC at a time.
In summary, AWS peering is a powerful feature that facilitates efficient communication between VPCs, making it a vital aspect of cloud infrastructure design.
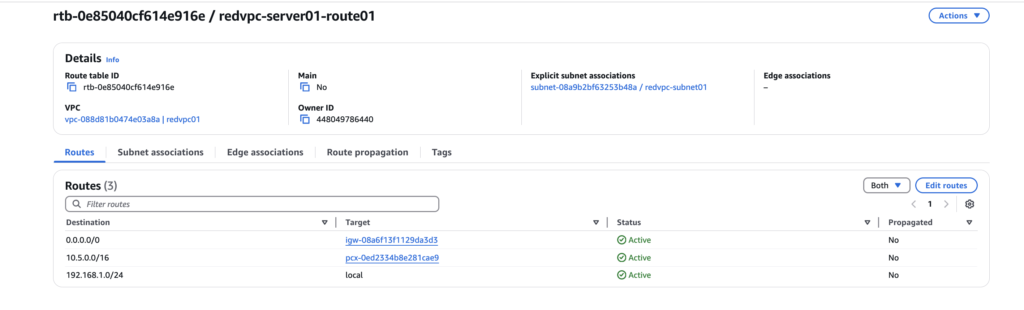
Navigate to the Route tables and select the previously created routes. Add the destination for the other VPC CIDR and set the target to Peering. Repeat this process for the other routes, as illustrated below, to establish communication effectively.
Now create EC2 instances and assign RedVPC to one instance and GreenVPC to another instance and check the communication.
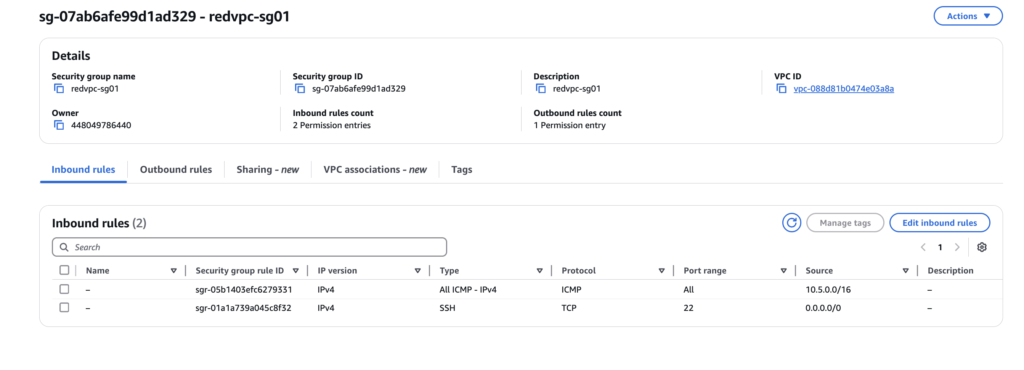
Note: If you did not enable the ICMP then ping will not work as like below. create Inbound rule in security group and attach to EC2 instances
Security Group: The Security Group in AWS (Amazon Web Services) is a vital component of cloud security management. It acts as a virtual firewall, controlling inbound and outbound traffic to your resources. By defining rules based on IP addresses, protocols, and ports, Security Groups help ensure that only authorized traffic can access your instances.
When you create a Security Group, you have the flexibility to customize it according to your specific needs. You can allow or deny traffic from specific IP ranges, enabling you to tailor access for different users and applications. Additionally, Security Groups are stateful, meaning that if you allow an incoming request from a specific IP address, the response is automatically allowed, regardless of outbound rules.
AWS Security Groups are essential for maintaining the integrity and security of your applications and data in the cloud, providing a robust layer of protection against unauthorized access.